《ISO/SAE 21434: 2021 Road vehicles — Cybersecurity engineering 道路车辆网络安全工程》标准解读之(3)
4.General considerations 总则 |
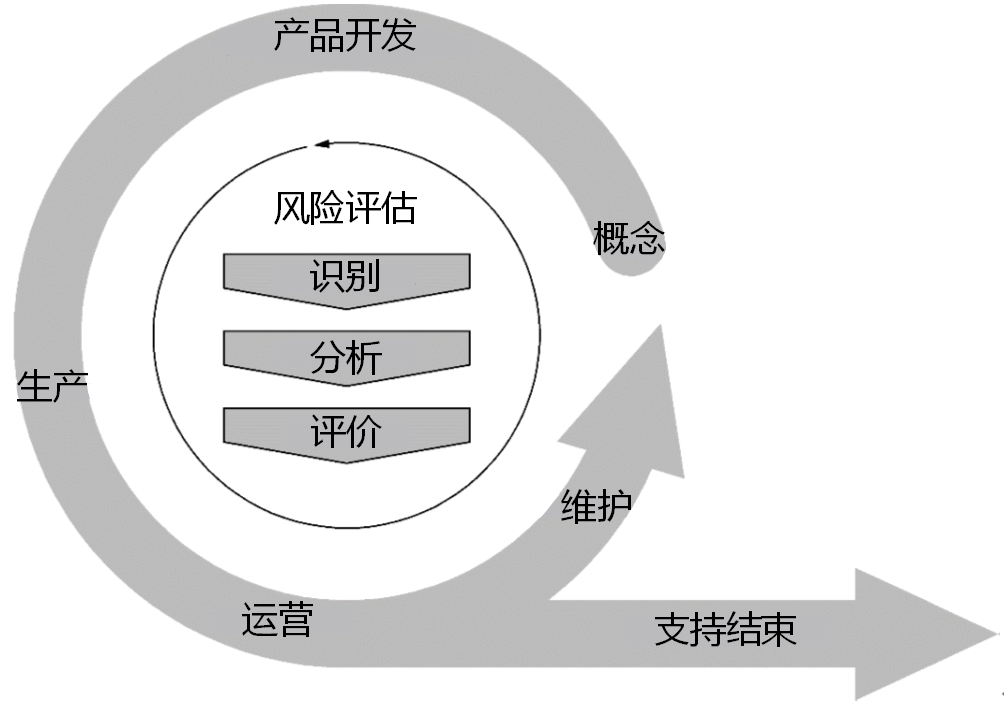
An item comprises all electronic equipment and software (i.e. its components) in a vehicle involved in the realization of a specific functionality at vehicle level, e.g. braking. An item or a component interacts with its operational environment. 项目包括涉及在车辆级实现特定功能的车辆中的所有电子设备和软件(即,其组件),例如,制动。项目或组件与其操作环境进行交互。 The application of this document is limited to cybersecurity-relevant items and components of a series production road vehicle (i.e. not a prototype) including aftermarket and service parts. Systems external to the vehicle (e.g. back-end servers) can be considered for cybersecurity purposes but are not in the scope of this document. 本文件的应用仅限于批量生产的道路车辆(即,非原型车辆)的网络安全相关项目和组件,包括售后市场和服务部件。出于网络安全目的,可以考虑车辆外部的系统(例如,后端服务器),但这不属于本文件的范围。 This document describes cybersecurity engineering from the perspective of a single item. The suitable allocation of functionality to items within the E/E architecture of a road vehicle is not specified in this document. For the vehicle as a whole, the vehicle E/E architecture or the set of the cybersecurity cases of its cybersecurity-relevant items and components can be considered. If cybersecurity activities described in this document are performed on items and components, then unreasonable vehicle cybersecurity risk is addressed. 本文件是从单个项目的角度来描述网络安全工程。在本文件中,没有对道路车辆的电子电器设备(E/E )的架构中的项目的功能的适当分配做出要求。对于整个车辆,可以考虑车辆电子电器设备(E/E )的架构或其网络安全相关项目和组件的网络安全案例集。如果在项目和组件上实施了本文件描述的网络安全活动,那么不合理的车辆网络安全风险就会被处理。 The overall cybersecurity risk management of an organization described in this document applies throughout all lifecycle phases as illustrated in Figure 2. 本文件中描述的组织的总体网络安全风险管理,适用于图2所示的生命周期的所有阶段。 |
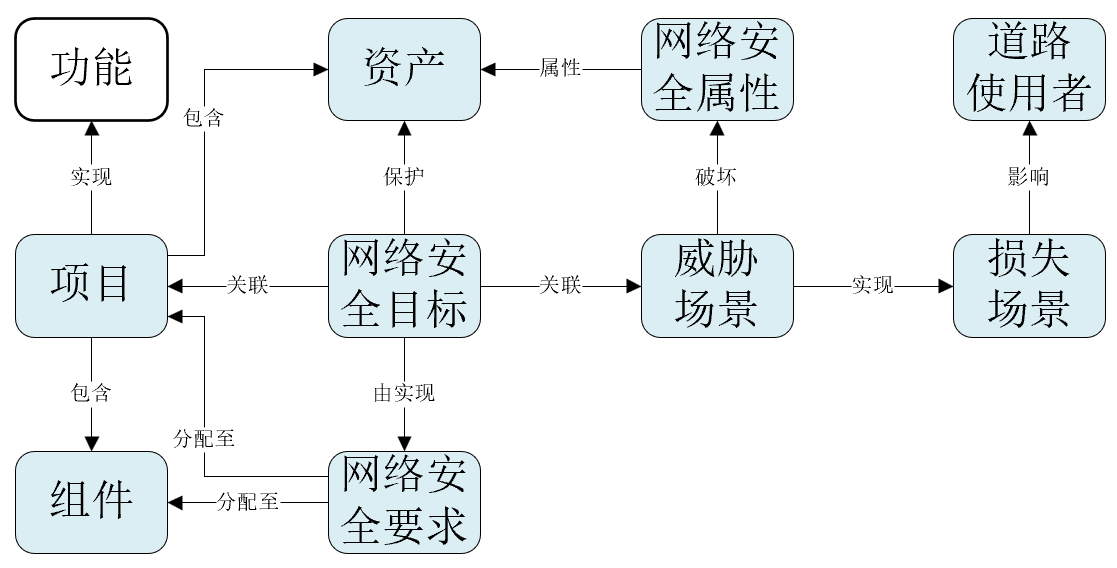
| Cybersecurity risk management is applied throughout the supply chain to support cybersecurity engineering. Automotive supply chains exhibit diverse models of collaboration. Not all cybersecurity activities apply to all organizations involved in a specific project. Cybersecurity activities can be tailored to accommodate the needs of a specific situation (see Clause 6). Development partners for a specific item or component agree on the work-split so that the applicable cybersecurity activities are performed (see Clause 7). 为支持网络安全工程,网络安全风险管理的应用是贯穿于整个供应链的。汽车供应链展示出合作的各样的模式。不是所有网络安全活动都适用于参与特定项目的所有组织。网络安全活动可以进行裁剪,以适应特定环境的需求(见条款6)。为了实施适宜的网路安全活动,参与特定项目或组件的开发伙伴应同意相关工作分工(见条款7)。 Figure 3 shows the relationship between an item, function, component and related terms. 图3显示了项目、功能、组件和相关术语之间的关系。 |
| Clause 15 describes modular methods for assessment of cybersecurity risk that are invoked in cybersecurity activities described in other clauses. 条款15描述了在其他条款所述的网络安全活动中调用的网络安全风险评估的模块化方法。 Analysis activities in the context of cybersecurity engineering identify and explore potential actions performed by abstract adversarial actors with malicious intent and the damage that can arise from the compromise of cybersecurity of the vehicle E/E systems. Coordination between cybersecurity engineering and expertise from other disciplines can support the in-depth analysis and mitigation of specific cybersecurity risks (cf. ISO/TR 4804 ). Cybersecurity monitoring, remediation and incident response activities complement concept and product development activities as a reactive approach acknowledging the changing conditions in the environment (e.g. new attack technologies) and the ongoing need to identify and manage weaknesses and vulnerabilities in road vehicle E/E systems. 通过网络安全工程的环境中分析活动,识别并探索具有恶意的抽象对抗行为者所实施的潜在行动,以及车辆电子电器设备(E/E )系统的网络安全的破坏带来的损害。网络安全工程与其他学科的专业知识之间的协作,可以支持对特定网络安全风险的深入分析和缓解(cf. ISO/TR 4804)。网络安全监测、补救和事件响应活动补充了概念和产品开发活动,作为一种认识到环境条件的变化(例如,新的攻击技术)的反应性方法,以及识别和管理道路车辆电子电器设备(E/E )系统的弱点和漏洞的持续需求。 A defence-in-depth approach can be used to mitigate cybersecurity risk. The defence-in-depth approach utilizes layers of cybersecurity controls to improve the cybersecurity of the vehicle. If an attack is able to penetrate or bypass one layer, another layer can help contain the attack and maintain protection of the assets. 可以使用深度防御方法来降低网络安全风险。深度防御方法利用网络安全控制层来改善车辆的网络安全。如果攻击能够穿透或绕过一层,另一层可以帮助遏制攻击并保持对资产的保护。 |
标准解读:
- 本条款是对ISO/SAE 21434:2021整体概述的一段文字,对ISO/SAE 21434:2021使用场景,实施ISO/SAE 21434:2021的整体方向以及实施ISO/SAE 21434:2021带来的价值;
- ISO/SAE 21434:2021适用于车辆中的所有电子设备和软件涉及的项目和组件,并且只适用于量产的项目和组件,不适用于原型件;
- 车辆外部的系统(例如,后端服务器),但这不属于本文件的范围,但是为了相关网络安全可以考虑,可以参考ISO/IEC 27001要求。
- ISO/SAE 21434:2021并非针对组织的整体信息安全管理的,而仅仅针对特定项目,如与道路车辆有关的项目。组织的整体信息安全管理可以采用ISO/IEC 27001,推荐使用BACCP工具;
- ISO/SAE 21434:2021,没有对道路车辆的电子电器设备(E/E )的架构中的项目的功能的适当分配做出要求,应根据项目实际情况结合ISO/SAE 21434:2021要求,做出合适的分配方案;
- 实施ISO/SAE 21434:2021整体思维是,结合产品生命周期(参考图2),进行风险评估,并采取合适的网络安全活动,以达到减缓网络安全风险,达到保护资产的目的;
- 如果在相关项目和组件上实施了本文件描述的网络安全活动,那么不合理的车辆网络安全风险就会被处理;
- 为了确保网络安全工程的实施,网络安全风险管理的应用是贯穿于整个供应链的,但不是所有网络安全活动都适用于参与特定项目的所有组织。网络安全活动可以进行裁剪,以适应特定环境的需求(见条款6);
- 为了实施适宜的网路安全活动,参与特定项目或组件的开发伙伴应同意相关工作分工(见条款7);
- 条款15提供了网络安全风险评估的方法;
- ISO/SAE 21434:2021实施过程中,可以通过分析活动识别和探索具有恶意的抽象对抗行为者实施的潜在行动以及车辆电子电器设备(E/E )系统的网络安全的破坏带来的损害;
- 实施ISO/SAE 21434:2021时,也可以采取其他关联的专业知识,如ISO/TR 4804来帮助ISO/SAE 21434:2021的实施,或相互协作;
- 实施ISO/SAE 21434:2021时,可以使用纵深防御方法来降低网络安全风险,以防止攻击穿透或绕过一层后,还有另一层可以帮助遏制攻击并保持对资产的保护;
- 在产品的开发、生产等活动中,必须要同时进行网络安全监测、补救和事件响应等活动,并且要随着环境条件的变化(例如,新的攻击技术)更新方案;
- 在产品的开发、生产等活动中,也要持续识别和管理道路车辆电子电器设备(E/E )系统的弱点和漏洞的。




