《ISO/SAE 21434: 2021 Road vehicles — Cybersecurity engineering 道路车辆网络安全工程》标准解读之(15)
| 6 Project dependent cybersecurity management 项目中必要的网络安全管理/6.1 General 总则 |
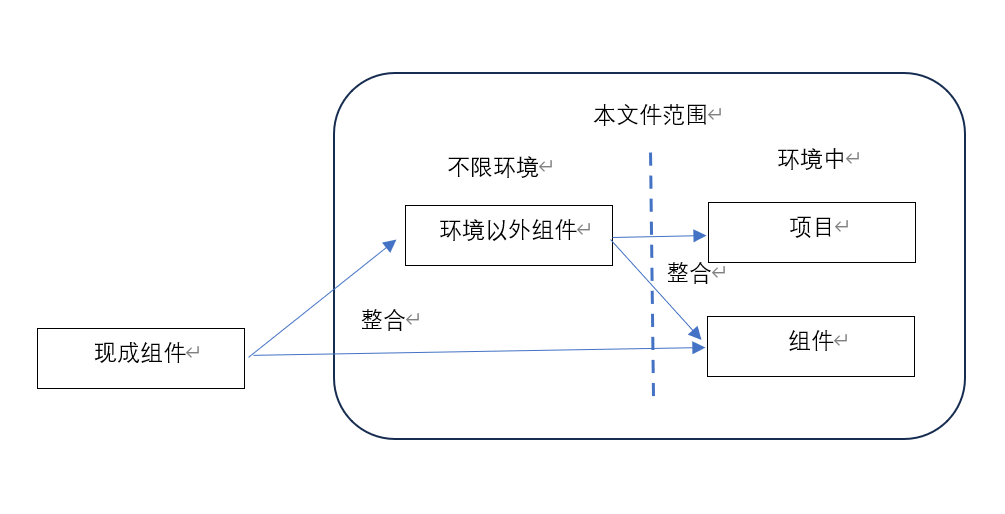
6.1 General 总则 This clause describes the requirements regarding the management of cybersecurity development activities for a specific project. 本条款描述了特定项目网络安全开发活动的管理相关的要求。 Project dependent cybersecurity management includes the allocation of responsibilities (see 6.4.1) and planning of the cybersecurity activities (see 6.4.2). This document defines requirements in a generic manner such that it can be applied to a variety of items and components. In addition, tailoring can be applied (see 6.4.3) that is based on a rationale and is defined in the cybersecurity plan. Examples of when tailoring can be used include: 项目中必要的网络安全管理包括分配职责(见6.4.1)和策划网络安全活动(见6.4.2)。本文件是以通用的方式定义了要求,以便可以适用于各类型项目和组件。此外,可以采用裁切(见6.4.3),但是要基于合理的理由,并在网络安全策划中对此进行定义。可以使用裁切的例子包括: — reuse (see 6.4.4), — 重复使用(见6.4.4), — component out-of-context (see 6.4.5), — 环境以外的组件(见6.4.5), — use of an off-the-shelf component (see 6.4.6), — 使用现成组件(见6.4.6), — update (see 13.4). — 更新(见13.4)。 Reuse of items and components is a possible development strategy that can be applied, with or without modifications to an item, component, or their operational environment. However, modifications can introduce vulnerabilities that might not have been considered for the original item or component. Furthermore, there might have been a change in known attacks, for example: 项目和组件的重复使用是一种可能的开发策略,可以在对项、组件或其运行环境进行修改或不修改的情况下对其进行采用。然而,修改可能引入在最初的项目或组件中可能未被考虑的脆弱性。此外,已知攻击可能已经发生了变化,例如: — an evolution of attack techniques, — 攻击技术的进化, — newly emerged vulnerabilities, e.g. learned from cybersecurity monitoring (see 8.3) and/or cybersecurity event evaluation (see 8.4), or — 新出现的脆弱性,如从网络安全监视(见8.3)和/或网络安全事态评估(见8.4)中学习到的, — a change of the assets since the original development. — 自从最初的开发以来的资产的变化。 If the original item or component was developed in accordance with this document, the reuse of that item or component is based on the existing work products. If the item or component was not originally developed in accordance with this document, the reuse can be based on the existing documentation with a rationale. 如果最初的项目或组件是根据本文件进行开发的,那么重复使用这些项目或组件可以基于现行的工作输出。如果项目或组件最初不是按照本文件进行的开发,那么重复使用可以基于现行文档,但需要说明合理的理由。 A component can be developed out-of-context, i.e. based on an assumed context. An organization can develop generic components for different applications and for different customers, prior to engagement or commercial agreement with a customer. The supplier can make assumptions about the context and intended use. Based on this, the supplier can derive requirements for the out-of-context development. For example, a microcontroller can be developed out-of-context. 组件可以在环境以外进行开发,如基于假定的环境。在与顾客达成约定或签订商务协议之前,组织可以为不同应用和不同顾客开发通用组件。供应商可以对环境和预期的使用进行假想。在此基础上,供应商可以推导出环境以外开发的需求。例如,微控制器可以在环境以外进行开发。 An off-the-shelf component is a component that is not developed on behalf of a specific customer and that can be used without modification of its design or implementation, e.g. a third-party software library, an open source software component. An off-the-shelf component is not assumed to have been developed in accordance with this document. 现成组件是指不是为特定顾客开发的组件,无需修改其设计或实施即可使用,如第三方软件库,开源软件组件。现成组件不被认为是按照本文件进行开发的。 Figure 5 shows that both an off-the-shelf component and an out-of-context component can be integrated into an item or component in accordance with this document. The integration can involve activities similar to reuse analysis in 6.4.4, and if changes are made to address invalid assumptions then change management (see 5.4.4) applies. The changes can be made to a component that is intended to be integrated and/or to the component or item that is the target of the integration. 图5展示了现成组件和环境外的组件可以根据本文件整合到项目或组件中。整合可以涉及类似6.4.4中重复使用分析的活动,以及如果为应对无效假定而做了变更,那么可以应用变更管理(见5.4.4)。可以对打算整合的组件和/或作为整合目标的组件或项目进行更改。 The cybersecurity case (see 6.4.7) is an input to a cybersecurity assessment and to the release for post-development. 网络安全实例(见6.4.7)是作为网络安全评估和后开发阶段发布的输入。 The cybersecurity assessment (see 6.4.8) judges independently the cybersecurity of an item or component and is an input for the decision to the release for post-development (see 6.4.9). 网络安全评估(见6.4.8)独立判定项目或组件的网络安全,并且作为后开发阶段(见6.4.9)发布决定的输入。 |
标准解析:
- ”6 项目中必要的网络安全管理“要求是针对特定项目开发活动的,而6.1则是对条款6的一个概述和说明。
- 在特定的项目进行时,一些必要的网络安全管理活动,如分配职责(见6.4.1)和策划网络安全活动(见6.4.2)等,必须要同时开展。
- 只要有合理的理由,一些要求是可以裁切的,裁切的要求要在网络安全策划中定义,例如,一些项目可能不会涉及到重复使用(见6.4.4),环境以外的组件(见6.4.5),使用现成组件(见6.4.6),更新(见13.4),那么就可以把这些要求裁切掉;
- 项目或组件是可以重复使用的,但需要考虑到因此而引入的脆弱性;
- 特定项目使用的组件(如环境以外的组件,现成组件),不一定是在项目特定环境下进行开发的,可以将这些组件整合到特定项目或组件中,整合过程可能涉及重复使用分析活动(见6.4.4),变更管理活动(见5.4.4)等。




